Explore Key Features of Conditional Access for Applications
Access Control That Goes Beyond the Network:
Work From Anywhere Means You Need Security Everywhere
Take a Smarter Approach to Conditional Access

Cloud-Native Architecture
Portnox is built from the ground up as a cloud-native solution, designed for modern IT environments.
- Deploys instantly with no on-prem hardware required
- Centralizes visibility across the network
- Scales seamlessly to meet organizational growth
- Updates continuously, saving IT teams from burdensome manual maintenance
Passwordless Authentication
Portnox replaces vulnerable passwords with secure, certificate-based authentication, eliminating credential-based attacks.
- Eliminates phishing risk
- Removes constant MFA prompts
- Better end-user experience, lower IT support costs

Stronger Security Controls
Portnox enforces real-time device security compliance before granting access to applications—and continuously monitors to eliminate endpoint risk.
- Evaluates device health and risk pre-access
- Enforces security policy compliance on all endpoints
- Blocks compromised, jailbroken, or non-compliant devices automatically
Automatic Remediation
Portnox’s conditional access goes beyond deny/allow/quarantine, delivering proactive, automated remediation without the need for IT involvement.
- Checks to ensure antivirus is up to date
- Ensures unauthorized peripherals do not connect
- Removes prohibited applications
- And more!
Works with Your Network
- IdPs and IAM solutions including Google Workspace, Okta, Entra ID, Active Directory, Ping, and more
- Supports both cloud and hybrid environments
- Works for all applications — SaaS, on-premise, and legacy apps
Zero Trust Principles
Portnox’s conditional access solution employs zero trust principles following the “never trust, always verify” framework.
- Follows least privilege and granular access controls
- Delivers fast, frictionless access
- Segments your network to prevent lateral movement
- Continuously monitors and evaluates trust based on user, device, and context
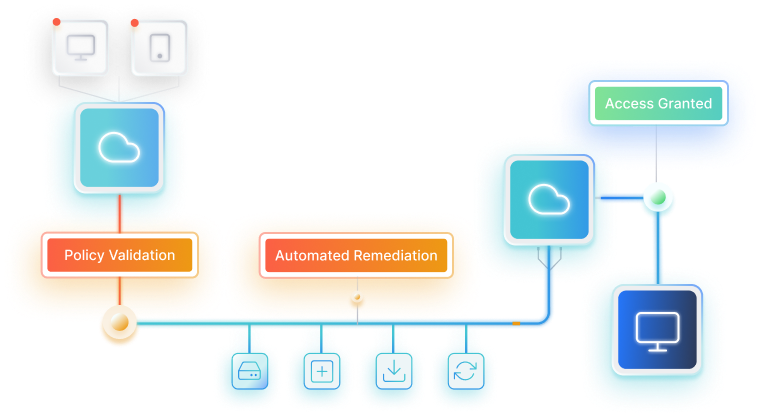
How It Works
Integrations
No need to reinvent the wheel—Portnox ZTNA’s conditional access provides many integrations that work within your existing security stack. You can be up and running, creating access policies in no time at all.


Security Tool Integration

Automatic Remediation
- Checks to ensure antivirus is up to date
- Ensures unauthorized peripherals do not connect
- Enforces policies set for OS and firewalls
- No VPNs, no agents, no on-premise servers required
- Faster deployment – get up and running in minutes, not weeks
- Reduces IT Overhead with passwordless authentication

Stronger Security Controls
- Evaluates device health, risk, and compliance pre-access
- Blocks compromised, jailbroken, or non-compliant devices automatically
- Works across all devices
- Evaluates device health, risk, and compliance pre-access
- Blocks compromised, jailbroken, or non-compliant devices automatically
- Works across all devices
Passwordless, Certificate-Based Authentication
- No passwords = No phishing risk
- Reduces MFA fatigue and bypass risks
- Better end-user experience, lower IT support costs
- No passwords = No phishing risk
- Reduces MFA fatigue and bypass risks
- Better end-user experience, lower IT support costs

Vendor-Agnostic & Compatible
- Google Workspace, Okta, Entra ID, Active Directory, Ping, and more
- Supports both cloud and hybrid environments
- Works for all applications — SaaS, on-premise, and legacy apps
- Google Workspace, Okta, Entra ID, Active Directory, Ping, and more
- Supports both cloud and hybrid environments
- Works for all applications —SaaS, on-premise, and legacy apps