Lock Down Application Access with Smarter Security, Simplified
Conditional Access for Your Applications with Portnox






No Passwords, No Problems
Passwordless Authentication
Passwords are weak, MFA isn’t enough—passwordless, certificate-based authentication boosts security, improves user experience, and cuts IT overhead.
Elevated Access Control
Endpoint Compliance
Ensure every device accessing your applications is secure and compliant while reducing risk through real-time endpoint posture checks.
Conditional Access For Your Applications With Portnox
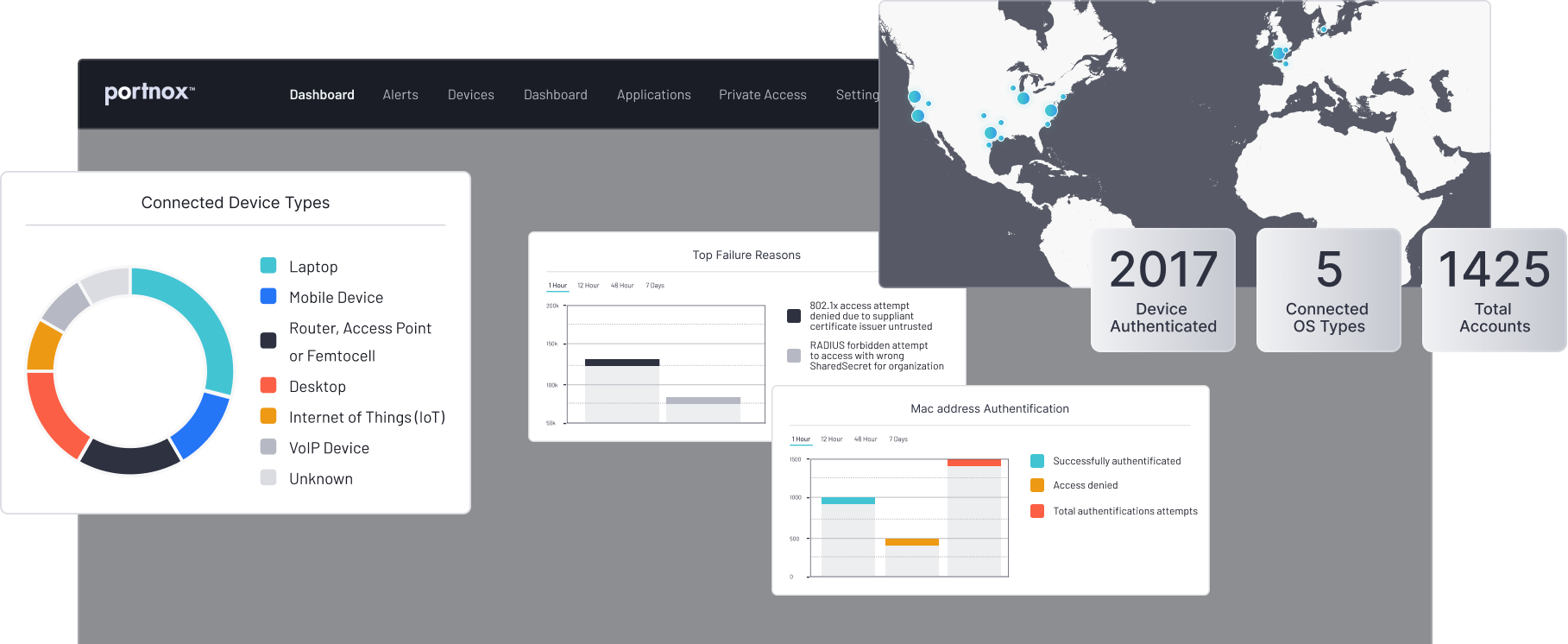
Key Capabilities
Define ironclad access policies tailored to your organization’s security needs. With real-time risk assessment, passwordless authentication, and endpoint compliance enforcement, you can ensure only verified devices and users connect—whether in the cloud or on-premise.
- Continuous enforcement – real-time device health checks before, during, and after access is granted.
- Seamless integration with identity providers and existing security ecosystems.
- Simple deployment – no on-premise infrastructure required.
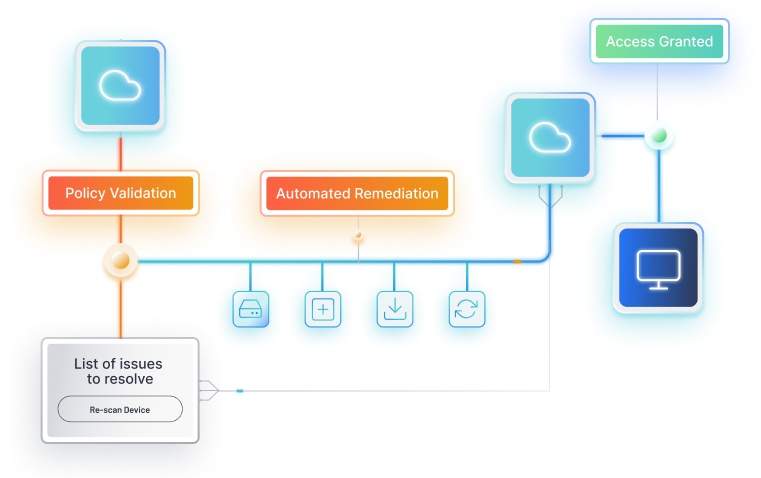
- Put Security on Autopilot with Portnox Conditional Access
Take Us for a Spin
Experience how easy it is to implement stronger access control and zero trust security with Portnox’s quick and easy approach.

Cloud-Native & Infrastructure-Free
- No VPNs, no agents, no on-premise servers required
- Faster deployment – get up and running in minutes, not weeks
- Reduces IT Overhead with passwordless authentication

Stronger Security Controls
Portnox enforces real-time device security compliance before granting access to applications.
- Evaluates device health, risk, and compliance pre-access
- Blocks compromised, jailbroken, or non-compliant devices automatically
- Works across all devices
Passwordless, Certificate-Based Authentication
- No passwords = No phishing risk
- Reduces MFA fatigue and bypass risks
- Better end-user experience, lower IT support costs

Vendor-Agnostic & Compatible
Portnox is vendor-neutral, integrating seamlessly with:
- Google Workspace, Okta, Entra ID, Active Directory, Ping, and more
- Supports both cloud and hybrid environments
- Works for all applications —SaaS, on-premise, and legacy apps
![]()
"Great Product and works as designed."
Kenneth W.
IT Security Manager
Mid-Market (51–1000 emp.)
![]()
"A breath of fresh air in the 802.1x field"
Verified User
Logistics and Supply Chain
Mid-Market (51–1000 emp.)
![]()
"Great Network Access Control Solution"
Yassine A.
Cyber Threat Analyst
Small-Business (50 or fewer emp.)
![]()
"Seamless integration with Microsoft Intune to extend a ZTNA Network"
Kyle N.
IT Supervisor
Small-Business (50 or fewer emp.)
![]()
"Easy to setup, deploy, manage and support."
Verified User
Financial Services
Enterprise (> 1000 emp.)
![]()
"Phenomenal product & service team from sales to implementation"
Jared P.
Director of IT
Mid-Market (51-1000 emp.)